A hash function is a mathematical algorithm that takes an input (or “message”) and returns a fixed-size string of characters, which is typically a hash value or digest (output). The output is a unique representation of the input data. You can think of a hash digest like a fingerprint. Just as every person’s fingerprint is unique, every message (input) processed by a hash function produces a unique digest (output). Even if two people are very similar, their fingerprints will still differ, just as small changes in input data will produce different digests. Hash functions are widely used in cryptography, data structures, and blockchain technology.
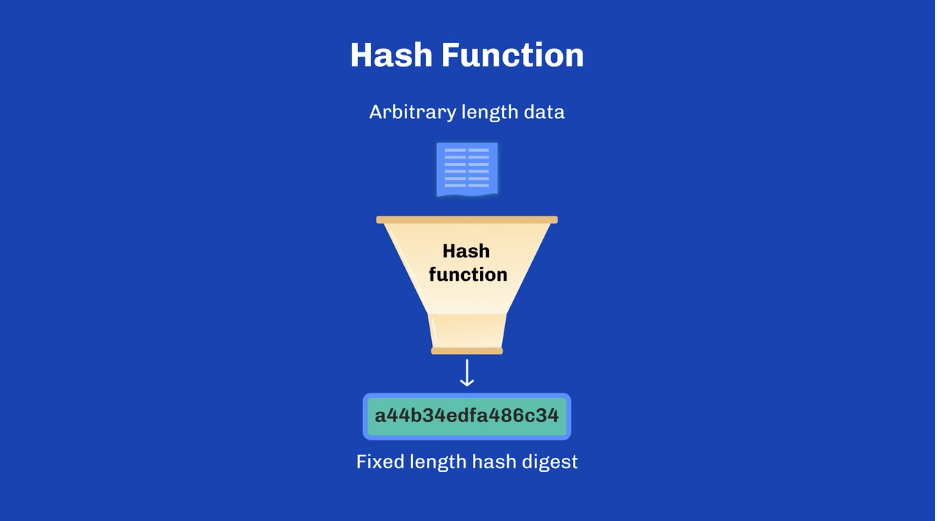
Key Properties of a Hash Function:
- Deterministic: A hash function always produces the same output for a given input. This means if you hash the same data multiple times, the output will always be identical.
- Fixed Output Size: Regardless of the size of the input, the hash function always produces a fixed-size output. For example, the popular SHA-256 hash function always produces a 256-bit hash, whether the input is a single letter or an entire document.
- Fast Computation: Hash functions are designed to be computed quickly, allowing for efficient use in many applications, such as data validation and encryption.
- Pre-Image Resistance: Given a hash value (output), it should be computationally infeasible to reverse-engineer or find the original input. This makes hash functions useful for security applications, like password storage.
- Second Pre-image Resistance: Ensures that, given an input and its hash output it is computationally infeasible to find a different input, such that the hash function produces the same output for both inputs. In practical terms, second preimage resistance means that even if someone knows the hash of a specific piece of data, they should not be able to craft a second, distinct piece of data that produces the same hash value.
- Collision Resistance: It should be highly unlikely that two different inputs will produce the same hash output (known as a “collision”). Strong collision resistance is important for maintaining the integrity of a system.
- Avalanche Effect: A small change in the input should result in a significantly different hash output. Even changing a single character in the input drastically changes the resulting hash.
Example: Hash Functions in the Cardano Blockchain
In blockchain systems like Cardano, hash functions are essential for ensuring security and data integrity. Here’s how they are used:
- Transaction Verification: When a transaction is broadcast to the Cardano blockchain, the details of that transaction are hashed. The resulting hash value uniquely identifies the transaction and ensures that no one can tamper with the transaction data without invalidating the hash.
- Block Creation: Every block in the Cardano blockchain contains a hash of the previous block. This creates a cryptographic link between blocks, forming the chain. If someone tries to modify any previous block, the hash would change, and the blockchain would immediately recognize the tampering.
- Proof-of-Stake (PoS): Cardano uses a consensus mechanism called Ouroboros, which relies on cryptographic hash functions to select validators who propose new blocks. Hash functions ensure that this process is secure and verifiable by all nodes.
In summary, a hash function is a crucial tool for cryptographic security, converting input data into a fixed-size string that is uniquely tied to the original data. In the Cardano blockchain, hash functions help ensure transaction integrity, secure block creation, and facilitate the overall security of the network.

Leave a Reply