Permissioned and Permissionless systems are two types of blockchain architectures that determine how participants can access, interact with, and contribute to the network. The key difference lies in who is allowed to participate and how control is managed across the network.
Permissioned Blockchain Systems
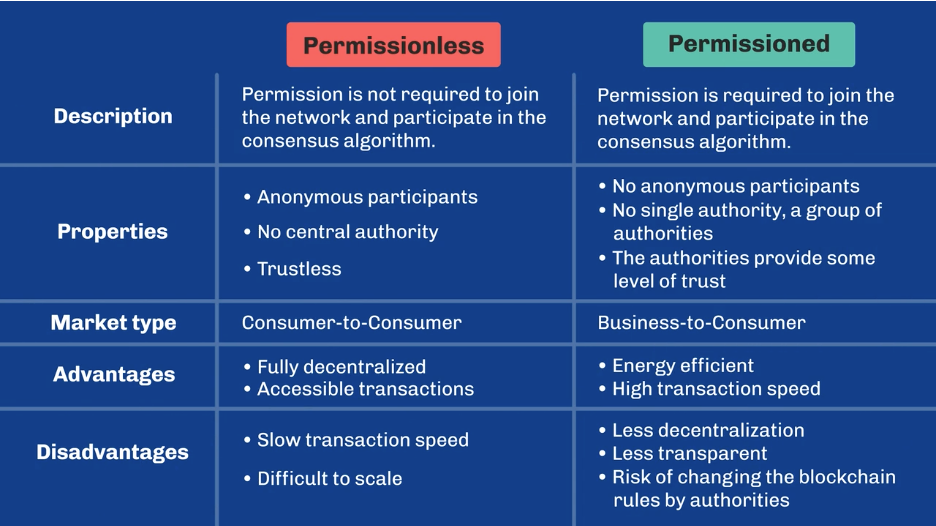
A permissioned blockchain restricts participation to a predefined group of entities. In these systems, only authorized participants are allowed to validate transactions, participate in the consensus mechanism, and access certain data on the network.
Key Characteristics
- Access Control: Only trusted and vetted participants can join the network. Permission is required to read, write, or validate data.
- Identity Verification: Participants typically need to be known and verified before they can participate in the network. This makes it easier to ensure accountability and compliance with regulations.
- Centralized Control: Permissioned systems often have a governing body or consortium that controls who can become a validator, participant, or node.
- Efficient Consensus: Since permissioned blockchains often have fewer participants and all are trusted entities, consensus mechanisms (such as Practical Byzantine Fault Tolerance (PBFT) or Proof of Authority (PoA)) can be more efficient compared to permissionless systems. This allows for higher throughput and lower transaction finality times.
- Use Cases: Permissioned blockchains are often used in enterprise settings, where privacy, efficiency, and control are critical. Examples include supply chain management, banking, and private consortiums.
Example
- Hyperledger Fabric is a permissioned blockchain framework designed for enterprise use, where only authorized organizations can operate nodes and perform transactions.
Advantages of Permissioned Systems
- Enhanced Privacy: Since only authorized parties can participate, permissioned systems can control data access and keep certain information private.
- Higher Efficiency: With fewer participants and trusted nodes, these systems often have faster transaction speeds and lower energy consumption.
- Regulatory Compliance: Since participants are known and controlled, it is easier to ensure compliance with legal and regulatory requirements.
Disadvantages of Permissioned Systems
- Centralization Risks: Permissioned blockchains can be more centralized, as a small group controls access and decision-making. This can reduce transparency and trustlessness.
- Limited Decentralization: The system relies on trusted parties, so it is not fully decentralized in the same way a public blockchain is.
Permissionless Blockchain Systems
A permissionless blockchain allows anyone to join the network, participate in consensus, validate transactions, and access data. These systems are typically open to the public, and no central authority controls who can participate.
Key Characteristics
- Open Access: Anyone can join the network without requiring permission or prior verification. This is what makes permissionless blockchains fully decentralized and public.
- Pseudonymous Participation: Participants often do not need to reveal their real-world identity. They interact with the network using cryptographic keys.
- Decentralized Consensus: Permissionless blockchains use consensus mechanisms like Proof-of-Work (PoW) or Proof-of-Stake (PoS), which are designed to operate in a decentralized environment where anyone can participate.
- Global Participation: Since anyone can participate, permissionless blockchains are open to users around the world, providing truly decentralized governance and decision-making.
- Use Cases: Permissionless blockchains are commonly used in public cryptocurrencies like Bitcoin, Ethereum, and Cardano. They are ideal for decentralized finance (DeFi), public cryptocurrencies, and other applications where openness, security, and decentralization are key.
Example
- Cardano is an example of a permissionless blockchain, where anyone can participate as a validator (staking ADA), become a node operator, or use the network without needing permission from a central authority.
Advantages of Permissionless Systems
- Decentralization: With no central control, permissionless blockchains are truly decentralized, meaning that they are resistant to censorship and single points of failure.
- Increased Security: Since anyone can join, permissionless systems often rely on robust cryptographic algorithms and consensus mechanisms like PoW or PoS to ensure the network remains secure.
- Trustless Environment: Participants don’t need to trust any single entity since the system operates transparently through consensus.
Disadvantages of Permissionless Systems
- Scalability Issues: Because anyone can join, permissionless blockchains often face challenges in scaling, leading to slower transaction speeds and higher costs, especially during periods of high demand.
- Energy-Intensive (for PoW systems): Proof of Work, which is used by Bitcoin and previously by Ethereum, is energy-intensive, as it requires significant computational resources to maintain network security.
Cardano: An Example of a Permissionless Blockchain
Cardano is a permissionless blockchain that uses a Proof-of-Stake (PoS) consensus mechanism called Ouroboros. The key features of Cardano as a permissionless system include:
- Open Participation: Anyone holding ADA, the native cryptocurrency of Cardano, can participate in the staking process to help secure the network. ADA holders can either delegate their stake to a pool or run their own staking pool.
- Decentralization: Cardano aims to be one of the most decentralized blockchain networks, with a large number of independent stake pools responsible for validating transactions and securing the network.
- Pseudonymous: Users can participate without revealing their real-world identities. Transactions are signed and validated using cryptographic keys, preserving privacy.
- Interoperability and Governance: As a permissionless system, Cardano’s future governance model is designed to be decentralized, allowing the community to propose and vote on network upgrades and changes without central authority control.
Hybrid Approaches
Some blockchains aim to combine aspects of both permissioned and permissionless systems. For instance, a consortium blockchain may allow a group of pre-approved participants (permissioned) but also allow some level of public interaction (permissionless). These hybrid systems balance decentralization, control, and efficiency.
Summary of Permissioned vs. Permissionless Systems
| Feature | Permissioned Blockchain | Permissionless Blockchain |
|---|---|---|
| Participation | Limited to authorized participants | Open to anyone |
| Identity | Participants are known and verified | Participants can remain pseudonymous |
| Consensus Mechanism | Often uses PoA or PBFT for efficiency | Uses PoW or PoS for decentralization and security |
| Control | Centralized or semi-centralized governance | Fully decentralized |
| Security | Security through trusted nodes | Security through decentralized consensus |
| Scalability | Highly scalable due to fewer participants | Can face scalability challenges |
| Use Cases | Enterprises, private institutions | Public cryptocurrencies, DeFi, decentralized apps |
| Example | Hyperledger, Ripple | Bitcoin, Ethereum, Cardano |
Conclusion
- Permissioned systems provide more control, privacy, and efficiency, making them suitable for enterprise or private use cases.
- Permissionless systems, like Cardano, offer openness, decentralization, and security, making them ideal for public cryptocurrencies and decentralized applications.
- Each system has its own strengths and weaknesses, and the choice between permissioned and permissionless often depends on the specific needs of the application, including factors like scalability, decentralization, and control.

Leave a Reply